5 Threat Intelligence Solution Use Cases

Key Takeaways
- The best threat intelligence solution for your organization will vary depending on your needs. Technology research company Gartner recommends taking a “use-case-centric” view when looking for the best solution for your organization.
- Effectively leveraging threat intelligence depends on the maturity of your organization’s security systems. Five example use cases demonstrate how threat intelligence is useful at a variety of maturity levels.
Identify Your Use Cases
Because threat intelligence solutions can be used in a wide variety of ways, it is important to identify your potential use cases before you choose a threat intelligence solution, rather than picking a solution and then trying to conform your use cases to the strengths of that solution. In its recent Market Guide, the technology research company Gartner suggests that end users of threat intelligence solutions identify their best solution by taking a “use-case-centric” approach.
For example, you may wish to gain insights into the identity, methods, and motives of threat actors targeting you so that you can avoid future threats and adjust or update your security; you may wish to create case studies for use in training exercises; or you may wish to gather more data so that you can prioritize vulnerability management based on the risks that your organization is particularly vulnerable to — Gartner provides a long list of possible use cases that are important to consider before choosing a solution.
5 Example Use Cases
Before making expensive and long-term decisions on how to improve your security programs, review Gartner’s five example below on the most effective uses of a threat intelligence solution.
1. Enriching Other Security Technologies by Integrating Threat Intelligence
These are the basics — integrating threat intelligence into your already existing security processes improves decision making for incident response and policy enforcement. According to Gartner, threat intelligence has recently begun to be widely incorporated into most security technology verticals, including security information and event management (SIEM), firewalls and unified threat management systems, intrusion detection and prevention, secure web gateways and secure email gateways, endpoint protection, web application protection, distributed denial of service, vulnerability management, security orchestration, and more.
If your organization does not already include threat intelligence in its security program, a good place to start is by looking at what you are already using and seeing how threat intelligence can make it more effective. Many threat intelligence solutions offer machine-readable intelligence that can integrate frictionlessly with the security products you already use, and an increasing number of solutions are using open-source standards, making it easier than ever to share data across platforms.
2. Vulnerability Prioritization
One of the best uses for threat intelligence is to gather data and perform analysis that will help your organization create a simple metric for evaluating vulnerabilities. This metric should be a measure of the overlap between the problems you can fix and the solutions that will make the biggest difference, given the time and resources available to you.
The traditional approach to prioritizing vulnerabilities comes from the attitude that the best security approach is to “patch everything, all the time, everywhere.” Achieving this goal would, in theory, lead to a perfectly impenetrable system — but it sets an impossibly high standard. So organizations who follow this approach will inevitably make compromises and go after the “biggest” problems first.
But, contrary to popular belief, the “biggest” problems (based on how much damage they actually cause) are not issues like zero-day threats or clever new exploits, but the same old vulnerabilities that continue to be exploited, precisely because so many organizations prioritize new threats instead of focusing on improving their fundamentals.
Threat actors are just as limited — if not more so — by time and the resources available to them as you are. They naturally will tend to use the simplest, least resource-intensive exploit as long as it continues to provide results. In its analysis of vulnerabilities discovered over the last decade, Gartner found that new vulnerabilities were found at a mostly steady rate, while the number of exploits grew exponentially over the same period, indicating that the vast majority of new exploits were actually variations on old ones — making it clear that any organization’s top priority should be patching already-known vulnerabilities rather than worrying about new threats.
3. Open, Deep, and Dark Web Monitoring
A good threat intelligence solution should gather its data from both open and closed sources on the internet.
Open sources, in short, are publicly available to everyone on the internet. This includes all the data that is indexed on search engines, which is sometimes called the surface web. Although this comprises some 4.56 billion pages, the public part of the internet only makes up about four percent of all data online.
The other 96 percent is divided between the deep web and the dark web. The deep web, which makes up about 90 percent of that data, refers to those parts of the internet that are locked away behind secure logins or paywalls, leaving them out of the reach of search engine crawlers. Most of this information includes scientific, academic, or government reports, personal information like financial records or medical histories, and private company databases.
The dark web, which makes up the remaining six percent of all the data on the internet, is made up of websites that can only be reached through browsers like Tor, which provide encryption and anonymity. Although this is not exclusively the case, many websites on the dark web provide marketplaces for illegal goods and services.
Vulnerabilities and their exploits are commonly discussed and traded in spaces on both the deep and dark web, both by parties that would wish to keep them safe, and by threat actors. That makes it essential to gather data from these sources to maintain a more comprehensive and up-to-date picture of what threats are out there.
Because accessing these spaces, particularly those on the dark web, requires more skill and comes with higher risks, one of the principal values of certain threat intelligence solutions is that they will do it for you. According to Gartner’s Market Guide, it can take many years of experience to effectively infiltrate these spaces and provide effective and timely analysis, and the best threat intelligence solutions will come with expert analysis that cannot be replicated by any algorithm.
4. Brand Monitoring
Although discussions about vulnerabilities and exploits will mostly take place in the closed parts of the internet, there is still great value in choosing a threat intelligence solution that will monitor open sources as well, particularly social media channels. Identifying threats in this arena is a skill in itself, requiring an awareness of your organization’s brand and the many ways a threat actor may seek to exploit it. Because these threats are appearing in public spaces and are subject to wider scrutiny, they can be more subtle, often relying on social engineering techniques instead of software exploits, and take a degree of expertise to recognize.
For example, a threat intelligence solution that includes brand monitoring may look for fake or malicious social media profiles that have been accepted by your staff or even mimic your staff’s profiles, identify malicious links that have been posted to your social media profiles, or even evaluate intellectual property loss and theft. Attacks that can be identified through social media and brand monitoring include phishing, false flag schemes, domain fraud, or activist or “trolling” attacks. Professionally developed threat intelligence solutions are much more efficient and will generate fewer false positives than open source tools or ad hoc approaches.
5. Threat Indicator Investigation, Enrichment, and Response
Not every attack can be prevented, of course, and one of the values of many threat intelligence solutions is their ability to improve the speed and accuracy of your incident response. In its guide, Gartner advocates shifting away from focusing on prevention toward a more balanced approach that also equally includes both detection and response.
Part of this framework includes rethinking how to prioritize vulnerabilities, as detailed above. It can also be helpful to have a threat intelligence solution that allows on-demand access to submit files or objects and looks for indicators of compromise like suspicious file hashes, domain names, or addresses, and compares them to the large datasets that some solutions maintain, enriching your organization’s data.
Some solutions even have the ability to go on the hunt for threats proactively. Whereas incident response is, by definition, a reactive process, more advanced solutions can seek out threats before they are actually implemented against your organization. Threat hunting takes a mature organization which already maintains the fundamentals of its security stance, like keeping its systems up to date and closely monitoring its own network, but provides an invaluable additional layer of security for those organizations that can do it effectively.
Another Framework for Evaluating Use Cases
Gartner’s Market Guide also provides an easy way to evaluate different threat intelligence services based on where they fall on two scales:
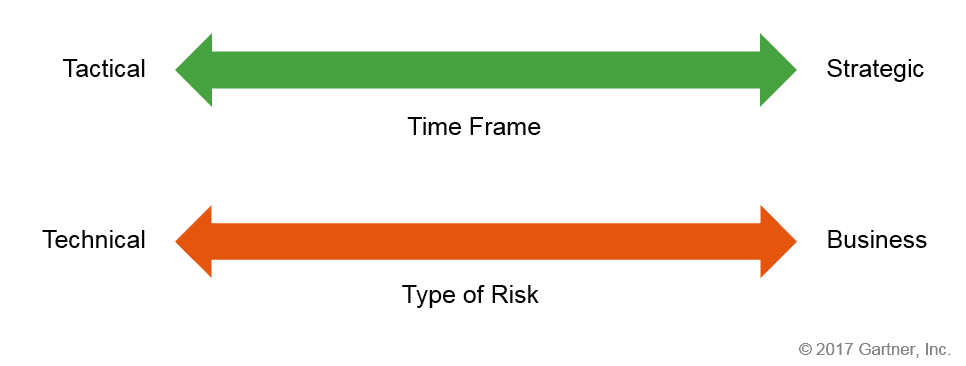
- Tactical — Strategic: This scale is a measurement of time. In rough terms, a tactical solution may be more effective in the short term, while a strategic solution will be better in the long term. For example, a solution might be considered more tactical if its strengths lie in its ability to quickly process data and identify threats, whereas a solution that offers deeper analysis that lends itself to long-term planning for the future could better be defined as strategic.
- Technical — Business: This scale is a measurement of risk type. In general terms, a technical solution will be more focused on security operations, while a business solution will deal with risk management. For example, a more technical solution might focus on indicators of immediate compromise like bad IP addresses or domains, but a solution that measures the risk from an emerging tactic or to a particular industry vertical is more aligned to business risk.
To get more details on the threat intelligence use cases as well as product and service suggestions, download your complimentary copy of Gartner’s “Market Guide for Security Threat Intelligence Products and Services.”
Related