Click for sound
45:17
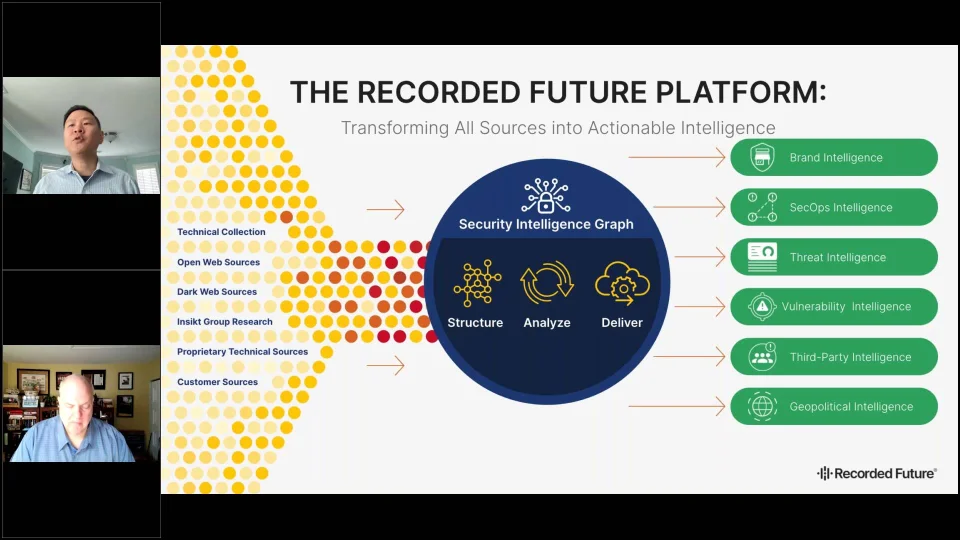
Join Allan Liska and David SooHoo in our webinar to dissect supply chain attacks and learn proactive measures for effective risk management
With third-party breaches at an all-time high, companies don’t have time to waste. Attackers are targeting third-party companies and software in order to gain access to your data and infrastructure. And as the SolarWinds breach proved, the effects of these attacks can be devastating. But what can you do to better manage your third-party risk?
Watch this on-demand webinar to hear from Recorded Future experts, Allan Liska and David SooHoo, who will show you how supply chain attacks happen by walking you through a case study — from leaked credentials appearing on the dark web to stolen data ending up on a ransomware extortion website.
Key Takeaways in this on-demand session:
- Understanding how modern supply chain attacks are carried out
- Seeing how third-party intelligence can identify early indicators of risk
- Learning the proactive measures you can take to mitigate supply chain risk
.
Upcoming Live Webinars: Our webinars feature insights from well-known security intelligence experts.
Related Resource: Learn more about what Recorded Future's researchers gleaned about the SolarWinds attack.



