Threat Intelligence in an Active Cyber Defense (Part 1)
Many organizations have bought into the idea of cyber threat intelligence but two questions tend to dominate the discussion: How do you use threat intelligence and when is an organization ready to use it? There are multiple answers to these questions but this two-part article offers an answer in the context of an active cyber defense.
An active cyber defense is the process of personnel taking an active and involved role in identifying and countering threats to the network and its systems. In contrast, a passive defense is software or hardware which can be added to the system or network for the purpose of increasing security without consistent input from personnel. An example would be an anti-virus system or a firewall.
It is key to note an active cyber defense is done internal to the network and is in no way related to “hack-back.” Active defense itself is a military strategy that has been used throughout history in land, air, and naval warfare. Unfortunately, when attempting to discuss this strategy in the context of “cyber” many individuals attempted to directly apply strategies of other fields into network security. This led to some confusion in academia publications, vendor marketing, and journalism which associated the term active defense with hack-back, counter strike, or other offensive actions. As it turns out, putting cyber in front of a word does not make it mean the opposite – active cyber defense is still about defense.
The Active Cyber Defense Cycle
One strategy for an active cyber defense is the Active Cyber Defense Cycle (ACDC). This cycle is comprised of four phases that work in conjunction to identify, counter, and learn from threats. These categories are: Threat Intelligence Consumption, Asset Identification and Network Security Monitoring, Incident Response, and Threat and Environment Manipulation. They will be discussed more in depth during the second part of this article.
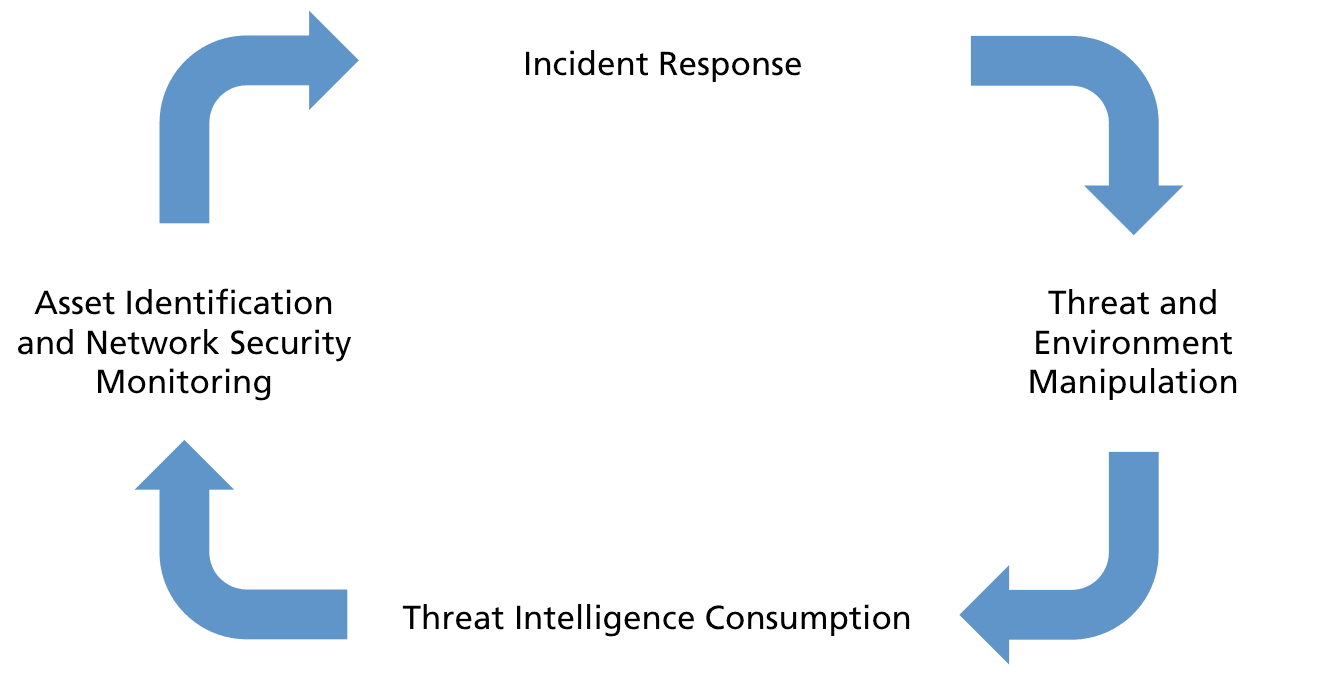
Figure: Active Cyber Defense Cycle
This strategy will feel familiar to many individuals who have taken part of teams such as Security Operations Centers (SOCs) or other type of threat operations centers. When building these types of active defense teams we often view the problem from a purely technical stance. Individuals are told the roles and responsibilities of popular SOCs and other teams attempt to copy those structures into their own organizations. This is often done without the intent of the process and focuses more on a purely technical solution. When security teams properly understand their organization and its mission though, requirements are better articulated and met. This is the purpose of having a strategy. It helps express the purpose of the defense and give guidance that can remain flexible to specialized and changing needs.
When is an Organization Ready?
Another advantage of using a strategy such as ACDC is it helps answer one of the two questions posed at the beginning of this piece: When is an organization ready to use threat intelligence?
The ability to use threat intelligence requires an organization be at the point they can use an active defense effectively and accomplish the other components of ACDC. To use an active defense, and in this case specifically ACDC, the organization must first have an understanding and a handle on architecture and passive defenses.
For architecture, this includes identifying the network topologies, such as what assets, ports, protocols, and data flows are on the network, and performing proper network health activities such as proper patching and configuration management.
Passive defenses such as firewalls, anti-virus, and intrusion prevention systems are used properly when an organization understands its architecture. Passive defenses can help fill the gaps in security once the architecture is understood as well as provide extra layers of security for critical systems. Architecture and passive defenses will never be perfect but there is a maximum regarding the return on investment that organizations must determine and meet appropriately.
It is after appropriate investments in architecture and passive defenses that there can be significant value added through an active defense. And through its association this is where threat intelligence becomes critical. Too often organizations attempt to utilize threat intelligence without first covering the basics or understanding its purpose – this is a losing struggle.
By comprehending that using threat intelligence is a key component of an active defense, which requires a certain security posture and maturity first, it is then possible to explore how to use threat intelligence. This will be discussed in the second part of this article.
Related